The term “firewall” often comes as a crucial element. Firewalls are essential to network security and help organizations maintain their network resources’ confidentiality, integrity, and availability.
You’ll learn more about this term if you’re wondering, “What is a Firewall?” and why it matters in this fast-evolving digital generation.
- What is firewall
- Different types of firewalls
- How do firewalls work?
- Benefits of Using a Firewall
- Challenges and Limitations using Firewalls
- Why firewalls are important?
- Firewall Features and Capabilities
- Best Practices for Firewall Configuration
- Future of firewalls
- How to Choose a Firewall
- Best Firewall
- Final Word
- FAQs
What is firewall
A firewall is a network security device that differentiates between a trusted internal network and an untrusted external network, such as the Internet. Its primary function is to monitor and control incoming and outgoing network traffic based on predetermined security rules.
Firewalls are designed to prevent unauthorized access to the network so as to avoid malicious activities such as hacking attempts, malware infections, and data breaches. They inspect network packets and apply security policies to allow or block traffic based on source and destination IP addresses, ports, protocols, and application types.
Firewalls can be implemented as a hardware device, software application, or a combination.
Different types of firewalls
Several types of firewalls are commonly used for network security. Some of the main types include:
1. Packet-filtering firewalls
A packet-filtering firewall examines every packet of data passing through the network. It allows or blocks packets based on predetermined rules and criteria, such as source or destination IP address, port number, or packet type. This is the most basic and commonly used type of firewall.
2. Stateful inspection firewalls
Stateful inspection firewalls not only inspect individual packets like packet-filtering firewalls but also monitor the state of the network connection. It keeps a record of the connections and their status so that it can decide whether to allow or block the traffic.
3. Proxy firewalls
Proxy firewalls act as intermediary servers between the internal and external networks. When a user requests data from an external server, the proxy firewall receives the request, verifies that the data is correct, and then forwards it on behalf of the user. With its use, the real identity of the user remains hidden, providing an additional layer of security.
4. Next-generation firewalls (NGFW)
NGFWs combine traditional firewall functionality with additional security features, such as intrusion detection and prevention systems (IDS/IPS), deep packet inspection (DPI), and application-aware capabilities. They provide more advanced protection against modern threats and offer enhanced visibility and control over network traffic.
5. Network address translation (NAT) firewalls
NAT firewalls are typically used in small office or home networks. They use network address translation techniques to map multiple internal IP addresses to a single external IP address, providing a level of protection by hiding the internal network structure.
How do firewalls work?
Firewalls inspect individual packets of data as they pass through the network. They compare specific information in each packet, such as source and destination IP addresses, port numbers, and protocols, against the predefined rules.
If a packet matches an allowed rule, it is allowed to pass through. Otherwise, it’s either blocked or flagged for further inspection.
In addition to packet filtering, many firewalls use a stateful inspection. This technique keeps track of the state of network connections. It monitors the data flow at the network layer and checks if incoming packets are part of established, legitimate connections.
Some firewalls perform a deep packet inspection at the application layer to analyze the content of network traffic to identify specific application protocols, detect threats, and enforce more granular security policies based on application-level data.
Firewalls use an access control list (ACL) to define rules and policies for allowing or blocking specific types of traffic. These rules can be based on IP addresses, port numbers, protocols, or other criteria. ACLs help administrators customize the firewall’s behavior to align with the organization’s security requirements.
When communicating with external networks, firewalls often employ network address translation (NAT) to translate private IP addresses used within an internal network to a single public IP address.
Benefits of Using a Firewall
Using a firewall can provide several benefits for individuals and organizations:
1. Network Security
A firewall acts as a barrier between an internal network and external networks, such as the Internet. It monitors incoming and outgoing network traffic, filtering and blocking potentially malicious data packets, unauthorized access attempts, and other cyber threats. By enforcing security policies, firewalls help protect sensitive data and prevent unauthorized network access.
2. Access Control
Firewalls allow administrators to set rules and control which network traffic is allowed or blocked. This enables organizations to restrict access to certain websites, applications, or services based on predetermined criteria. By implementing access control policies, firewalls help prevent unauthorized access to sensitive resources and reduce the risk of data breaches.
3. Threat Prevention
Firewalls have various security mechanisms, including intrusion detection and prevention systems (IDS/IPS) and threat intelligence feeds. These features help identify and block known threats and suspicious activities in real time. By detecting and mitigating potential threats, firewalls enhance overall network security and reduce the risk of successful cyber attacks.
4. Network Monitoring and Logging
Firewalls provide logs and reports that contain information about network traffic, attempted connections, and security events. This data can be analyzed to identify potential security risks, track network usage patterns, and investigate security incidents. Network monitoring and logging capabilities offered by firewalls help organizations maintain network visibility and facilitate incident response and forensic analysis.
5. Compliance and Regulatory Requirements
Many industries have specific security and compliance standards that organizations must adhere to. Firewalls are crucial in meeting these requirements by providing network segmentation, access control, and security monitoring. Implementing a firewall can help organizations demonstrate compliance with regulations such as the Payment Card Industry Data Security Standard (PCI DSS) or the Health Insurance Portability and Accountability Act (HIPAA).
Challenges and Limitations using Firewalls
1. Complexity
Firewalls are complex to configure and manage, especially for organizations with large and complex networks. Managing and properly configuring it requires a deep understanding of network protocols, ports, and security policies.
2. False Positives and False Negatives
Firewalls use rule-based filtering to allow or deny network traffic. Sometimes, they may incorrectly identify legitimate traffic as malicious (false positive) or fail to detect malicious traffic (false negative), which can impact the network’s security.
3. Encrypted Traffic
Firewalls have difficulties inspecting encrypted traffic, such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS). This limitation can be exploited by attackers who hide malicious activities within encrypted connections.
4. Limitations in Application Visibility
Traditional firewalls focus on network-level filtering, which means they may not have granular visibility into specific applications or protocols. This can make it challenging to enforce security policies for individual applications or identify potentially risky behavior.
5. Evolving Threat Landscape
Firewalls need regular updates to keep up with emerging threats and attack techniques. However, the rapidly evolving nature of cyber threats means firewalls may face challenges in effectively detecting and defending against new and sophisticated attacks.
6. Single Point of Failure
Firewalls act as a gatekeeper between internal and external networks. If a firewall fails or experiences a vulnerability, it can become a single point of failure, potentially leaving the network vulnerable to attacks.
Also Read:
- What is Ethical Hacking? Everything you need to know
- Best Laptops for Cyber Security
- What is a VPN? Everything You Need To Know
Why firewalls are important?
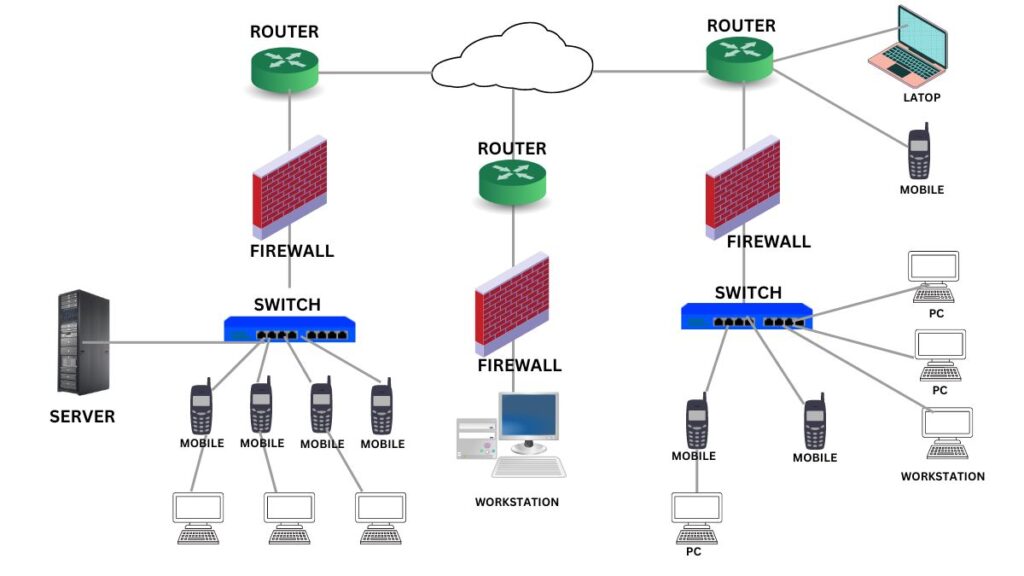
Firewalls are important for several reasons:
1. Network Security
Firewalls provide an important layer of security for computer networks. These help prevent unauthorized network access to our systems and protect sensitive data from being compromised by external threats such as hackers, malware, or unauthorized users.
2. Traffic Control
A firewall has predefined security rules based on which it monitors incoming and outgoing network traffic. They analyze data packets thoroughly and determine whether to allow or block them based on factors such as IP address, port, protocol, and application type. By controlling traffic flow, a firewall prevents malicious or suspicious activities from reaching the network.
3. Protection Against Cyber Attacks
Firewalls act as a barrier between an internal network and the external Internet. They actively monitor and filter incoming traffic, blocking potential cyber-attacks such as Distributed Denial of Service (DDoS) attacks, brute force attacks, or intrusion attempts.
4. Application Security
Firewalls can also provide application-level security by inspecting the content of network packets. They can identify and block malicious code or suspicious activities within the data transmission, protecting against threats such as viruses, worms, or Trojan horses.
5. Compliance Requirements
Many industries and organizations have specific regulatory compliance requirements related to network security. Firewalls are often a mandatory component of these requirements, ensuring that organizations meet the necessary standards for data protection and network security.
Firewall Features and Capabilities
Firewalls are crucial for network security, shielding systems from unauthorized access and harmful activities. They offer various important features:
1. Packet Filtering: Firewalls check data packets in the network, following rules to block or allow based on criteria like IP addresses, ports, and protocols.
2. Stateful Inspection: Stateful inspection firewalls monitor network connections, distinguishing between legitimate and unauthorized ones. This helps block specific attacks, like IP spoofing, with advanced decision-making.
3. Application-Level Gateway (Proxy): Some firewalls act as application proxies, adding extra security by inspecting and filtering specific app or protocol traffic between clients and servers.
4. Intrusion Detection and Prevention System (IDPS): Some advanced firewalls have IDPS features that detect and prevent attacks by analyzing network traffic patterns and comparing them to a database of known attack signatures.
5. Virtual Private Network (VPN) Support: Firewalls often include VPN features for secure remote access, and encrypting traffic between users and internal networks for privacy and security on public networks.
6. Logging and Reporting: Firewalls create network activity logs, useful for troubleshooting, compliance, and security audits. They offer detailed reports on traffic patterns and security events.
Best Practices for Firewall Configuration
Regarding firewall configuration, there are several best practices to consider.
1. Determine your network requirements
Understand your network infrastructure, including the number of users, devices, and the types of applications and services that need to be accessed. This will help you identify the specific needs and requirements for your firewall.
2. Define security policies
Establish clear security policies that outline what traffic is allowed or blocked by the firewall. Consider your organization’s specific needs, such as the level of access required for different user groups or the types of protocols and services that must be allowed.
3. Regularly update firewall firmware and software
Keep the firewall up to date with the latest firmware and software patches provided by the vendor. This ensures the firewall has the latest security updates and protections against emerging threats.
4. Implement default deny rule
Configure the firewall to have a default deny rule, meaning all traffic is blocked unless explicitly allowed. This approach minimizes the risk of unauthorized access.
5. Use application-aware filtering
Implement firewall rules that filter traffic based on specific applications or services, rather than solely relying on port numbers or IP addresses. This allows for more granular control and better protection against application-level threats.
6. Enable logging and monitoring
Enable firewall logging and monitoring capabilities to track and analyze network traffic. This helps identify suspicious or malicious activities and provides valuable insights for troubleshooting and incident response.
7. Regularly review and update firewall rules
Periodically review and update firewall rules to ensure they align with your organization’s evolving network requirements and security policies. Remove any unnecessary rules and update existing rules to reflect changes in your network infrastructure.
Future of firewalls
The future of firewalls is evolving to keep up with the changing threat landscape and technology advancements. Some key trends include:
1. Next-Generation Firewalls (NGFWs)
NGFWs integrate advanced features like intrusion prevention, application control, and threat intelligence. They provide more granular control and visibility, enabling organizations to protect their networks better.
2. Cloud-based Firewalls
With the rise of cloud computing, firewalls are being deployed as virtual instances. Cloud-based firewalls offer scalability, flexibility, and centralized management across distributed environments.
3. Integrated Security Platforms
Firewalls are integrated into broader security platforms, providing a unified network security approach. This integration allows for better coordination and correlation of security events and policies.
4. Machine Learning and AI
Firewalls incorporate machine learning and AI technologies to improve threat detection and response capabilities. These technologies can analyze large amounts of data and identify patterns to detect and prevent emerging threats
How to Choose a Firewall
When choosing a firewall, consider the following factors:
1. Security features
Assess the firewall’s security features, such as intrusion prevention, antivirus, web filtering, and application control capabilities. Choose a firewall that aligns with your organization’s security needs.
2. Scalability
Consider the scalability of the firewall to accommodate future growth in your network infrastructure. Ensure the firewall can handle increasing traffic volumes and support additional users and devices.
3. Vendor reputation and support
Research the reputation and reliability of the firewall vendor. Look for vendors with a strong track record in providing regular updates and support for their products.
4. Compatibility
Look for a firewall solution with a user-friendly interface and intuitive management tools. Assess the ease of configuration, monitoring, and ongoing maintenance. Consider whether it integrates with your existing management systems.
6. Budget considerations
Determine your budget for firewall implementation, including upfront costs, licensing fees, and ongoing maintenance expenses. Consider the total cost of ownership over the expected lifespan of the firewall solution.
7. Conduct a proof of concept (POC)
If possible, perform a POC with shortlisted firewall solutions to evaluate their effectiveness in your specific environment. Test the performance, security features, and compatibility with your network infrastructure.
8. Consult with experts
Seek advice from network security professionals or consultants who can provide insights based on their expertise and experience. They can help identify specific requirements and recommend appropriate firewall solutions.
Best Firewall
Determining the “best” firewall depends on various factors, including specific requirements, budget, and the environment in which it will be deployed. Several well-regarded firewall vendors are in the market, each with strengths and capabilities.
1. Palo Alto Networks
Palo Alto Networks is Known for its advanced threat prevention capabilities and integration of network security features.
| Feature | Description |
|---|---|
| App-based Policy Enforcement | Identify and control applications and block malicious ones. |
| User Identification | Identify and control applications, and block malicious ones. |
| Threat Prevention | Guard against intrusion malware and filter URLs to prevent various threats. |
| URL Filtering | Filter web traffic by criteria like URL category, reputation, and content. |
| Data Loss Prevention (DLP) | Block unauthorized transfer of sensitive data. |
| SD-WAN | Guard against intrusion and malware, and filter URLs to prevent various threats. |
| GlobalProtect | Secure remote access for employees working from home or on the go. |
| IoT Security | Ensure security for IoT devices with visibility and control (Prisma IoT). |
2. Cisco
Cisco offers various firewall solutions, including its Adaptive Security Appliance (ASA) and Firepower Next-Generation Firewall (NGFW) series.
| Feature | Description |
|---|---|
| Stateful Inspection | Tracks connections, allowing only legitimate traffic. |
| Application Awareness and Control | Monitors and controls applications to prevent threats. |
| Integrated IPS | Detects and blocks malicious traffic for network safety. |
| URL Filtering | Blocks access to specific websites, enhancing security. |
| Cloud-Delivered Threat Intelligence | It can be managed efficiently using tools like Cisco Firepower Management Center and Cisco SecureX. |
| Advanced Threat Protection | Offers sandboxing and malware analysis for robust security. |
| Scalability | Available in various sizes for businesses of all scales. |
| High Availability | Configurable for continuous operation even on device failure. |
| VPN Support | Supports secure connections to remote networks. |
| Security Management | Can be managed efficiently using tools like Cisco Firepower Management Center and Cisco SecureX. |
3. Fortinet

The Fortinet is Known for its FortiGate NGFWs, which provide comprehensive security features and performance.
| Feature | Description |
|---|---|
| UTM | Combines antivirus, intrusion prevention, web filtering, and more into a single platform. |
| Stateful Inspection | Monitors and controls traffic based on active connections. |
| IPS | Detects and prevents network attacks, including malware and exploits. |
| VPN Support | Enables secure communication over public networks with VPN technologies. |
| App Control | Monitors and controls specific applications within the network. |
| Web Filtering | Controls website access, blocking malicious content and enforcing policies. |
| SSL Inspection | Analyzes encrypted traffic for potential threats through SSL/TLS inspection. |
| Adv. Threat Protection | Offers sandboxing and threat intelligence for defense against sophisticated threats. |
| Cloud Integration | Integrates with cloud services for consistent security policies. |
| Security Fabric | Utilizes a coordinated approach with different components sharing threat intelligence. |
| High Availability | Supports configurations for continuous operation despite hardware or software failures. |
| Logging and Reporting | Provides comprehensive logging and reporting for analyzing network activity and security events. |
| Wireless Security | Includes features for managing and securing wireless networks. |
| IPv6 Support | Ensures compatibility with the latest Internet Protocol standards. |
4. Check Point
Check Point Firewall offers a range of firewall solutions, including its Next Generation Firewall (NGFW) and Security Gateway appliances.
| Feature | Description |
|---|---|
| Stateful Inspection | Monitors connections for context-based decision-making. |
| IPS | Detects and prevents various network attacks. |
| App Control | Monitors and controls specific applications. |
| URL Filtering | Controls website access for enhanced security. |
| VPN Support | Enables secure communication for remote access. |
| Threat Intelligence | Integrates feeds to stay updated on the latest threats. |
| Advanced Threat Prevention | Utilizes SandBlast for sophisticated threat mitigation. |
| Identity Awareness | Integrates with identity solutions for granular control. |
| Logging and Monitoring | Provides comprehensive tracking and analysis capabilities. |
| Mobile Access | Facilitates secure access for remote users. |
| High Availability | Supports configurations for continuous operation. |
| Multi-Domain Management | Centrally manages security policies across domains. |
5. Juniper Networks
The Juniper Networks is Known for its SRX Series Services Gateways, which provide advanced security features and scalability.
When selecting a firewall solution, assessing individual needs and considering factors such as performance, scalability, ease of management, and compatibility with existing infrastructure is recommended. Consulting with security professionals or engaging with vendors directly can help identify the most suitable firewall for specific requirements.
| Feature | Description |
|---|---|
| Security Zones | Combines antivirus, antispam, and web filtering into one platform. |
| Stateful Inspection | Monitors connections for context-aware decisions. |
| IPS (Intrusion Prevention) | Detects and prevents various network attacks. |
| VPN Support | Enables secure communication via VPN technologies. |
| UTM | Combines antivirus, antispam, web filtering into one platform. |
| App Visibility and Control | Monitors and controls application-level traffic. |
| Web Filtering | Controls website access, blocking specific URLs. |
| Dynamic VPN | Allows on-demand secure connections for remote users. |
| Threat Intelligence Integration | Integrates threat intelligence feeds for enhanced detection. |
| High Availability | Configurations for continuous operation and failover. |
| Logging and Reporting | Comprehensive logs and reports for tracking network activity. |
| Security Intelligence | Leverages real-time security intelligence services. |
| DDoS Protection | Features for mitigating Distributed Denial of Service (DDoS) attacks. |
| IPv6 Support | Supports IPv6 for compatibility with the latest standards. |
Final Word
To deal with cyber threats, the firewall is like a wall that strengthens the network against malicious activities. They play an important role in protecting network security by monitoring and controlling incoming and outgoing traffic based on predefined rules.
Initially, it served only as a packet-filtering mechanism, but today, it blocks threats from many unknown networks. This is a testament to our unwavering commitment to the security of the digital domain. Its only job is to protect, defend, and secure our network.
FAQs
Yes, there are free firewall options available. Two popular ones are:
1. Windows Defender Firewall (for Windows
2. iptables (for Linux)
No, a firewall cannot prevent all cyberattacks and threats. While it helps block unauthorized access, other security measures, like antivirus software and safe online practices, are needed to enhance overall protection.
Firewalls alone may not effectively protect against phishing attacks and spam. Specialized tools like email filters and user education are also crucial to enhance protection against these threats.
Firewalls can sometimes have a minor impact on internet speed or network performance, but modern firewalls are designed to minimize these effects. The benefits of enhanced security usually outweigh any slight decrease in speed.